You will need to have a MetroMap Enterprise plan to access single-sign-on (SSO) service. This is currently available for Azure Active Directory.
Azure Active Directory Single Sign-On (Azure AD SSO)
Azure Active Directory Single Sign-On (Azure AD SSO) automatically signs users in when they are on their corporate devices connected to their corporate network. By using Azure AD SSO, users will not need to type in their username or password to sign into MetroMap MapViewer.
This feature provides the user with easy access to the web-based application without needing any additional on-premises components. It allows users to sign into both on-premises and cloud-based applications using the same passwords. This feature provides a better user experience - one less password to remember and reduces IT helpdesk costs because users are less likely to forget how to sign in.
When users sign in using Azure AD SSO, this feature validates users' passwords directly against the on-premises Active Directory.
Benefits of using this service:
Better User Experience
Same passwords to sign into on-premises and cloud-based applications.
Less time is taken to resolve password-related issues.
Simplified Administration
No need for complex deployments, IP filtering or other types of network configuration.
No need to change settings frequently.
More Secure
On-premises passwords are never stored in the cloud in any form.
Protects your user accounts by working seamlessly with Azure AD Conditional Access policies, including Multi-Factor Authentication (MFA), blocking legacy authentication and filtering out brute force password attacks.
Communication between an application and Azure AD is secured using certificate-based authentication. These certificates are automatically renewed every few months by Azure AD.
On-boarding Process and Account Management
To enable MetroMap’s Azure AD SSO login, your organisation’s Account Admin will need to contact your MetroMap Account Manager or write to support@metromap.com.au.
We will add your entity’s email domain to allow our authentication system to recognise users within your organisation. We will then create an Enterprise Subscription for your organisation, and the users within your organisation who use MetroMap services will stay under this subscription. The administrator(s) of your account will have the ability to manage the users within the subscription through our MetroMap User Management Portal.
To provide the best user experience and services, we will request a user’s email address, first name, last name, and phone number (if applicable) during the user’s login process. We use the user’s email as a unique identifier to allow that user to store uploaded geometry files on our MetroMap MapViewer. If necessary, our support team can provide one-to-one support services via phone or email.
Once we have enabled SSO with Azure Active Directory, your organisation’s IT department (or relevant team) will need to configure the Admin Consent Workflow for the MetroMap application within their Azure Portal. Please see this Azure documentation for more details: https://learn.microsoft.com/en-us/entra/identity/enterprise-apps/configure-admin-consent-workflow
Once the enrolment process is finished, users will be able to use our seamless login process for MetroMap MapViewer.
User Sign-in Flow with MetroMap:
The user tries to access the MetroMap MapViewer
If the user is not signed in, they will be redirected to the Azure AD sign-in page.
The user enters their email and password into the Azure AD sign-in page and selects the Sign-in button.
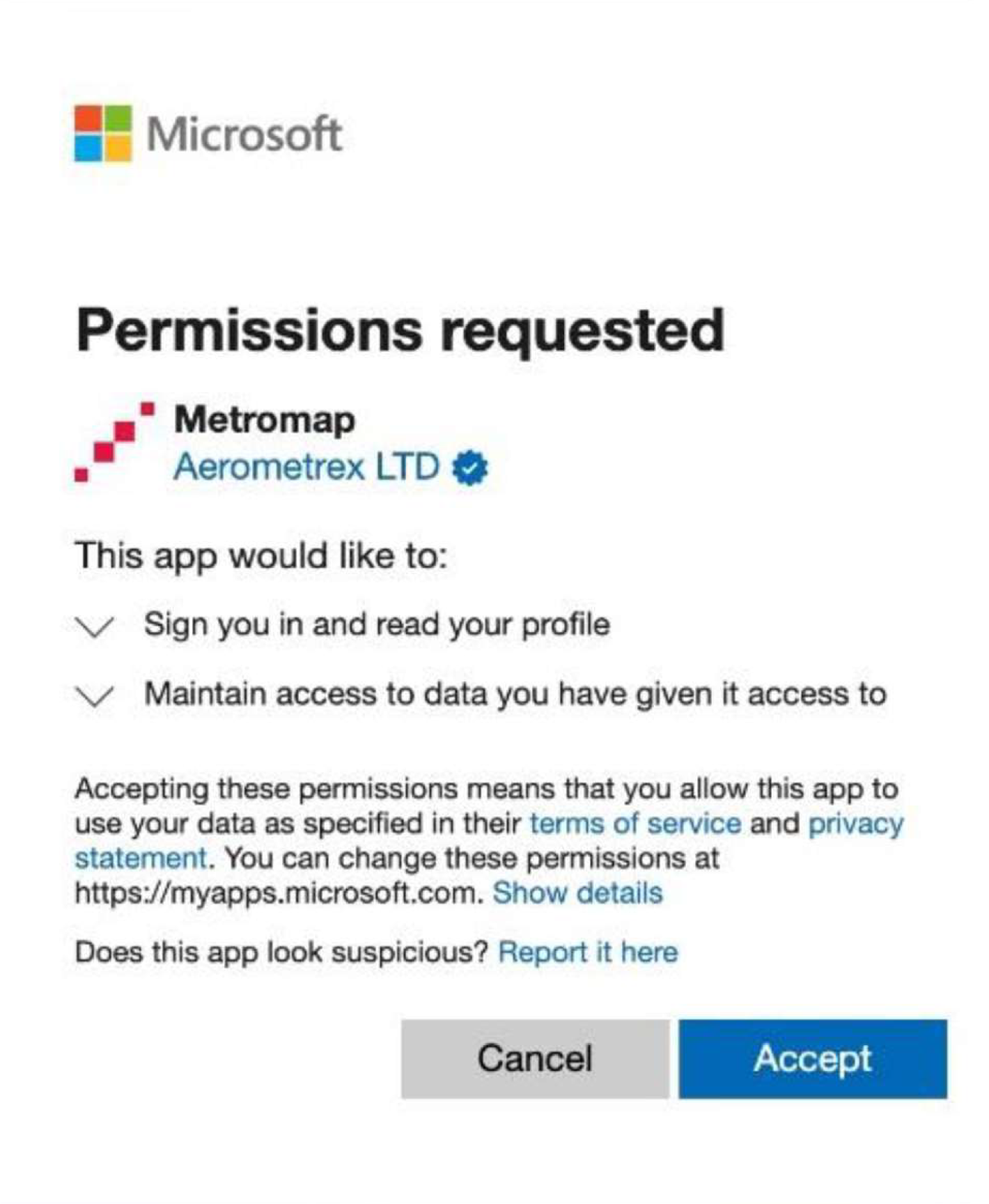
For a first-time user, the Azure AD sign-in page will then redirect the user to the Microsoft Permissions acknowledgement page (see image below):
"Sign you in and read your profile" – email, first name, last name, and phone number (if applicable) to provide our basic services.
"Maintain access to data you have given it access to" - allows MetroMap MapViewer to keep the user signed in for an extended time.
The Active Directory Domain Controller (DC) evaluates the request and returns the appropriate response (success, failure, password expired, or user locked out) to MetroMap.
If the user sign-in is successful, they can access the MetroMap MapViewer and use the web application.